AzureWireGuard - An Azure ARM template to quickly setup your own WireGuard VPN Server.
AzureWireGuard - The quickest way to setup your own modern VPN server. This is an Azure ARM template that you can quickly deploy to setup your own WireGuard VPN Server with auto-configured server and client configurations. All server configuration steps are taken care of and five ready to use client configuration files are generated. You just have to download them and configure your WireGuard clients to use them.
WireGuard VPN is a rethink of how VPN software are designed and is receiving genuine appreciation from the community. WireGuard works by adding a network interface wg0 (similar to eth0 or wlan0), and any network traffic that is routed to this interface gets securely encapsulated and sent over UDP to its peer. The packets between these peers is encrypted using public-key(asymmetric) cryptography. The peers have to generate and share the public keys with one another and use them while setting up the network interface.
This Azure ARM template simplifies the setup process by scripting all the required steps; it does the following
- Create an Ubuntu Server Virtual Machine.
- The only inputs you provide are the administrator username and password.
- The name of all resources are generated automatically to avoid any conflicts.
- Install WireGuard Server.
- Configure WireGuard Server
- Create Private and Public Keys for Server and Client.
- Create the Server Configuration.
- The WireGuard interface IP address is set to 10.13.13.1.
- Setup NAT on the server to forward client traffic to the internet.
- Start the WireGuard Interface.
- Configure WireGuard to auto start even after a reboot.
- Generate five client configuration files, which you can download and start using.
- The five clients are given the IP addresses 10.13.13.101, 10.13.13.102, 10.13.13.103, 10.13.13.104 and 10.13.13.105.
- The Client DNS server is set to 1.1.1.1.
- Enable UFW firewall.
- Install Ubuntu Server Upgrades.
- Schedule a reboot after 24 hours, to ensure all Ubuntu Server Upgrades are applied.
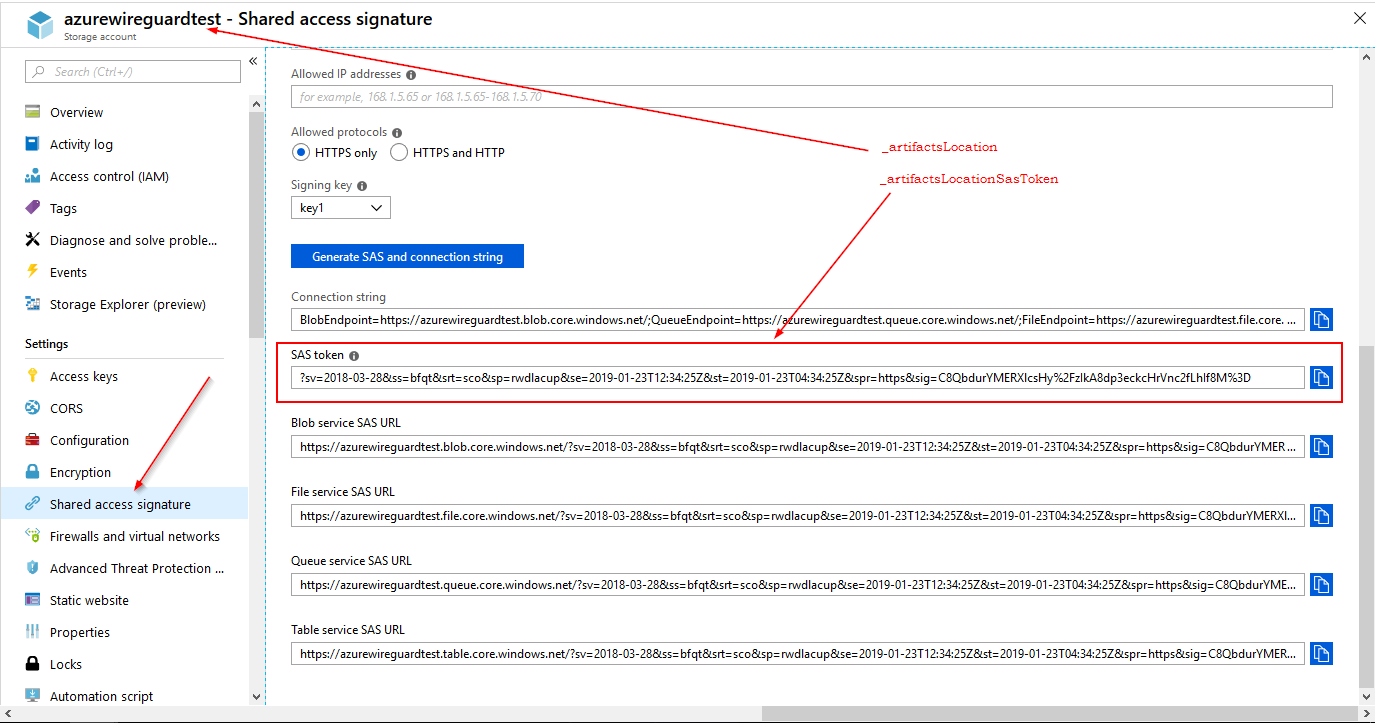
You can deploy this Azure ARM template with one of the following methods. Some knowledge of how Azure ARM templates work is really helpful. Azure ARM needs a Storage Account (_artifactsLocation) with access controlled via a Shared access signature (_artifactsLocationSasToken), to upload this template while deploying. If you use Visual Studio this Storage Account is created automatically in the Resource Group called ARM_Deploy_Staging.
Method 1 - From Visual Studio
- Clone the git repository.
- Open the solution file in Visual Studio and deploy from Visual Studio.
Method 2 - From Azure Deploy
- Create a storage account (you can also use an existing one) for ARM to upload this template. (_artifactsLocation)
- Create a Shared access signature (SAS Token) for that storage account with full permissions. (_artifactsLocationSasToken)
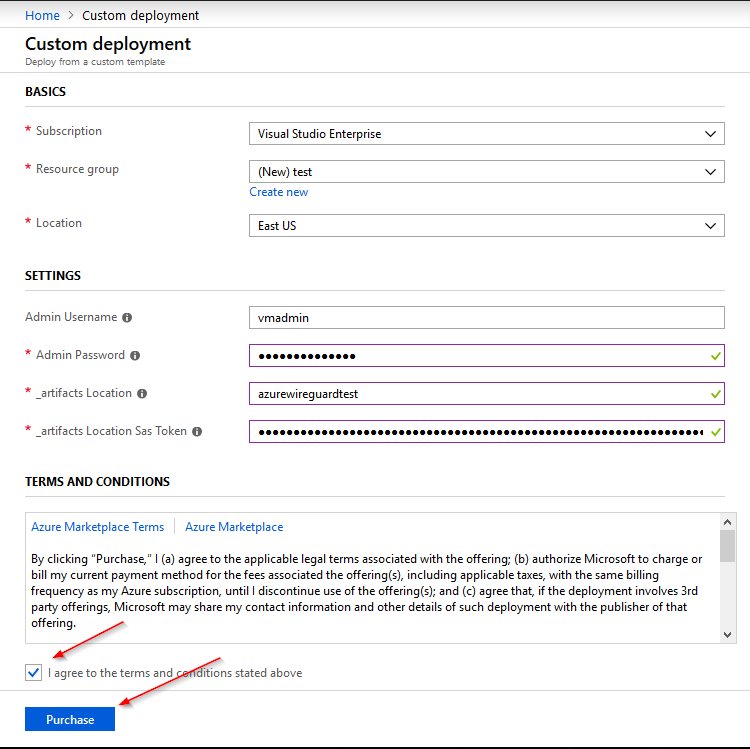
- Hit the Deploy to Azure button.
- Fill the necessary parameters along with _artifactsLocation and _artifactsLocationSasToken from above and hit the Purchase button.
Other Methods
- There are multiple ways to deploy an Azure ARM template like Powershell, Azure CLI, Azure Portal and REST API.
This Azure ARM template creates five ready to use WireGuard client configuration files. The client configuration files are named wg0-client-one.conf, wg0-client-two.conf, wg0-client-three.conf, wg0-client-four.conf and wg0-client-five.conf and are located in the administrator user’s home folder (~/).
You can use tools like scp or pscp to download the client configuration files directly from the server.
scp <admin-user>@<server-fqdn>:/home/<admin-user>/wg0-client-one.conf /local/dir/
pscp <admin-user>@<server-fqdn>:/home/<admin-user>/wg0-client-one.conf c:\local\
Example: scp vmadmin@awgyj5lzwixbj3ng.westus.cloudapp.azure.com:/home/vmadmin/wg0-client-one.conf /local/dir/
If you are going to use these client configuration files on Windows clients, just remember these configuration files have Linux Line Endings (LF) while Windows WireGuard clients would expect DOS Line Endings (CRLF).
The AzureWireGuard ARM template is available on GitHub. Feel free to contribute.